
Spain’s Ministry of the Interior has announced the arrest of 16 individuals connected to the Grandoreiro and Melcoz (also known as Mekotio) cybercrime groups. Both are originally from Brazil and form part of the Tetrade umbrella, operating for a few years now in Latin America and Western Europe.
Grandoreiro is a banking Trojan malware family that initially started its operations in Brazil. Similarly to two other malware families, Melcoz and Javali, Grandoreiro first expanded operations to other Latin American countries and then to Western Europe. We have witnessed Grandoreiro’s campaigns since at least 2016, with the attackers regularly improving techniques, striving to stay undetected and active for longer periods of time. Based on our analysis of campaigns we have seen Grandoreiro operate as a Malware-as-a-Service (MaaS) project.
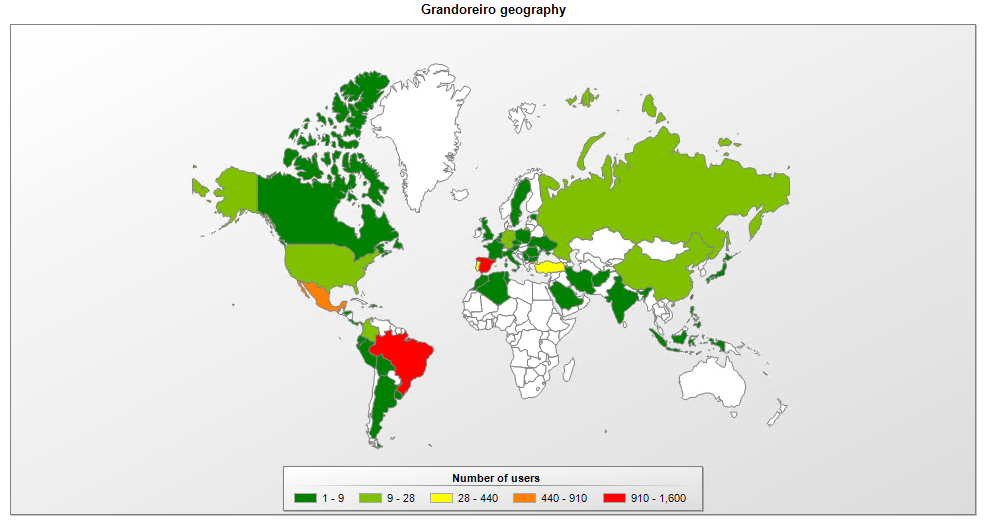
Since January 2020, our telemetry shows that Grandoreiro has attacked mostly Brazil, Mexico, Spain, Portugal, and Turkey.
On the other hand, Melcoz (also known as Mekotio) is a banking Trojan family developed by the Tetrade group which has been active since at least 2018 in Brazil, before they decided to expand overseas. We found the group attacking assets in Chile in 2018 and, more recently, in Mexico. There are also likely victims in other countries, as some of the targeted banks have international operations. Generally, the malware uses AutoIt or VBS scripts, added into MSI files, which run malicious DLLs using the DLL-Hijack technique, aiming to bypass security solutions. This malware steals passwords from browsers and from the device’s memory, providing remote access to capture internet banking access. It also includes a Bitcoin wallet stealing module.
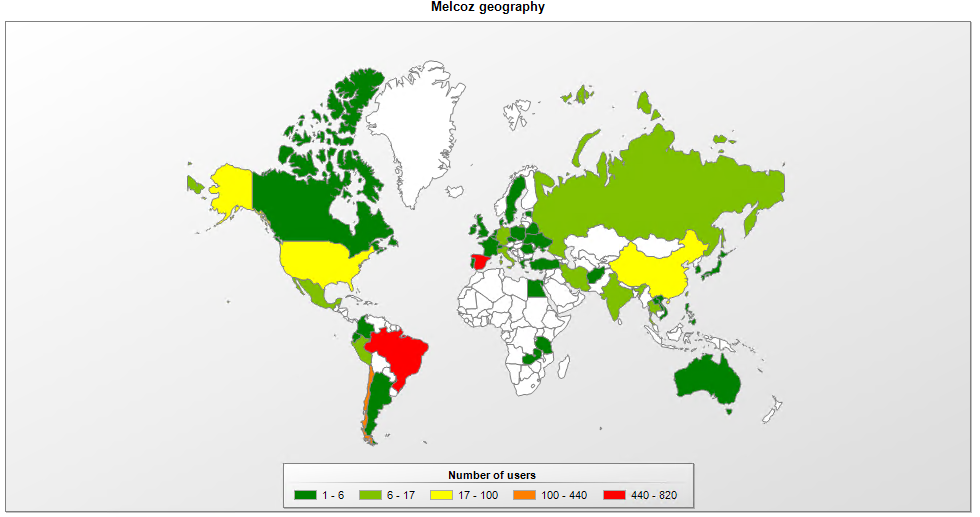
Our telemetry confirms that since January 2020, Melcoz has been actively targeting Brazil, Chile, and Spain, among other countries.
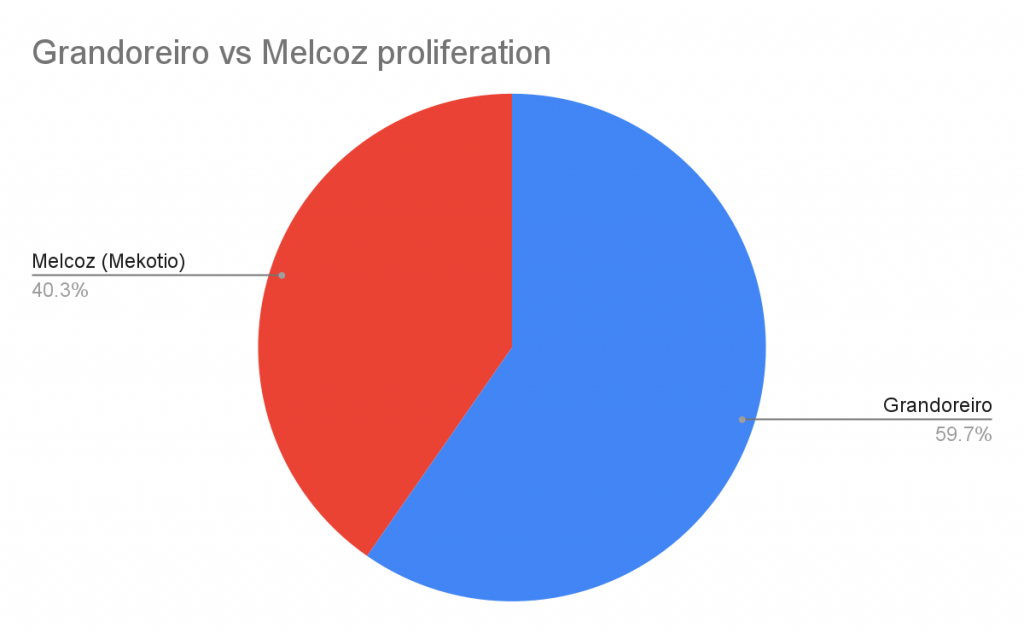
If we compare Grandoreiro and Melcoz in terms of proliferation, it’s clear that Grandoreiro is more aggressive when targeting victims worldwide.
What can we now expect after the arrest of 16 individuals in Spain? The work carried out by the Guardia Civil of Spain in actioning these arrests is remarkable. However, since both malware families are from Brazil, the individuals arrested in Spain are just operators. In other words, the creators of Grandoreiro and Melcoz will likely remain in Brazil where they may develop new malware techniques and recruit new members in their countries of interest.
Kaspersky technologies detect both families as Trojan-Banker.Win32.Grandoreiro and Trojan-Banker.Win32.Melcoz.
We recommend that financial institutions stay vigilant and watch the threats that are part of the Tetrade umbrella closely while improving their authentication processes, boosting anti-fraud technology and threat intel data, and trying to understand and mitigate such risks. Detailed information about Tetrade with full IOCs and Yara rules and hashes of these threats is available to our Financial Threat Intel services users.
Arrests of members of Tetrade seed groups Grandoreiro and Melcoz





















Demostenes Fermin Iturrizaga Huaman
Yes.The Members Of Ransomware Will Be See…